On Thursday, September 30th there will be a small change in how older browsers and devices will treat Let's Encrypt's certificates. While most sites will be unaffected, it will likely impact you if you're providing an API or support IoT devices.
TL;DR:
- Let's Encrypt's DST Root CA X3 root certificate will expire on September 30th, but Let's Encrypt's newer ISRG Root X1 root certificate has already been deployed, meaning all sites will automatically keep working on all relatively modern devices.
- A lot of older devices, however, will stop working, as they haven't been receiving updates (meaning: they aren't aware that ISRG Root X1 is a trusted root certificate).
- There is a workaround for older Android versions, which Let's Encrypt have implemented. It works by keeping the expired DST Root CA X3 certificate active as well.
- Because this Android workaround is enabled by default, some versions of OpenSSL/GnuTLS/LibreSSL (which are used on lots of IoT devices) will start failing on September 30th due to a bug.
- The way to work around this bug is to "prefer" the ISRG Root X1 certificate, which Forge now supports, but doing so disables the Android workaround.
What is changing?
In short, Let's Encrypt's cross-signed DST Root CA X3 certificate is about to expire. This certificate has been around since their launch back in October 2015, with almost every device (and browser) being able to rely on it.
Fortunately, Let's Encrypt has been hard at work ever since their launch, and have created their own root certificate called "ISRG Root X1". By working together with all major browsers and operating system developers, this certificate has since been included in pretty much all modern devices.
On May 4th, Let's Encrypt already deployed the necessary changes, and have been serving a combination that includes both this new ISRG Root X1 certificate, as well as the expiring DST Root CA X3 certificate. This way, modern browsers that are aware and trust this new ISRG Root X1 certificate will use this, while older browsers that don't know / don't trust this certificate (due to not receiving software updates that includes it) can still use the DST Root CA X3 until it expires on September 30th.
(Part of) The Problem
Once this DST Root CA X3 does expire on September 30th, a wide range of older devices that haven't been receiving software updates to include the new ISRG Root X1 certificate, will suddenly be unable to make requests to Let's Encrypt secured websites & API's.
While there is a limited workaround for Android (see below), our recommendation is to do either of the following things if you absolutely need to support devices running old operating systems such as the iPhone 4 or Ubuntu 14.02:
- Purchase your own SSL certificate (from a different supplier, such as Comodo) and use that instead of Let's Encrypt.
- Manually import the new ISRG Root X1 certificate into the affected device's certificate Key Store.
- Use an up-to-date version of Firefox, which uses it's own built-in Key Store instead of the one provided/included with the Operating System.
With that said, the by-far best solution to this problem is to instead take the opportunity to drop support for these devices altogether. While this might seem like a harsh choice, the fact that these devices haven't received the ISRG Root X1 certificate as part of their updates almost certainly also indicates that they haven't been receiving other important security updates either.
This means that the continued use of such devices isn't just a potential risk to the end-user that visits your website(s) and uses your platform(s), but it could also negatively impact your website/platform/company's reputation in the event that their device being hacked leads to their credentials being used maliciously to (for example) extract private data from your platform or to perform actions such as the permanent deletion of data.
A workaround for Android
Due to a design decision in Android (>= 2.3.6 && <= 7.1.1), certificates that are considered to be so-called 'trust anchors' remain valid even after they are considered expired.
This means that if Let's Encrypt keeps using the expired DST Root CA X3 certificate after September 30th, those versions of Android will remain able to visit Let's Encrypt secured websites until early 2024, and that's exactly what they've decided to do by default.
Great! Maximum compatibility. Problem solved! 🚀
.. yet another problem (for IoT devices)
While the decision to support legacy Android devices by including the expired certificate is a great one, its continued inclusion unfortunately causes another problem:
Due to a bug in some versions of OpenSSL (1.0.0 - 1.0.2), GnuTLS (< 3.6.14), LibreSSL (< 3.2.0) and perhaps other TLS/SSL libraries as well, Let's Encrypt's certificates will be seen as invalid as a result of this invalid DST Root CA X3 certificate still being included.
This might cause problems for a lot of IoT devices, as these devices more often than not do not receive software updates and likely still rely on these libraries.
The Solution
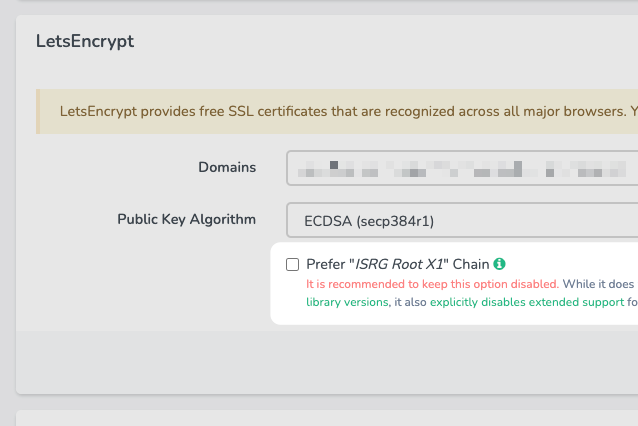
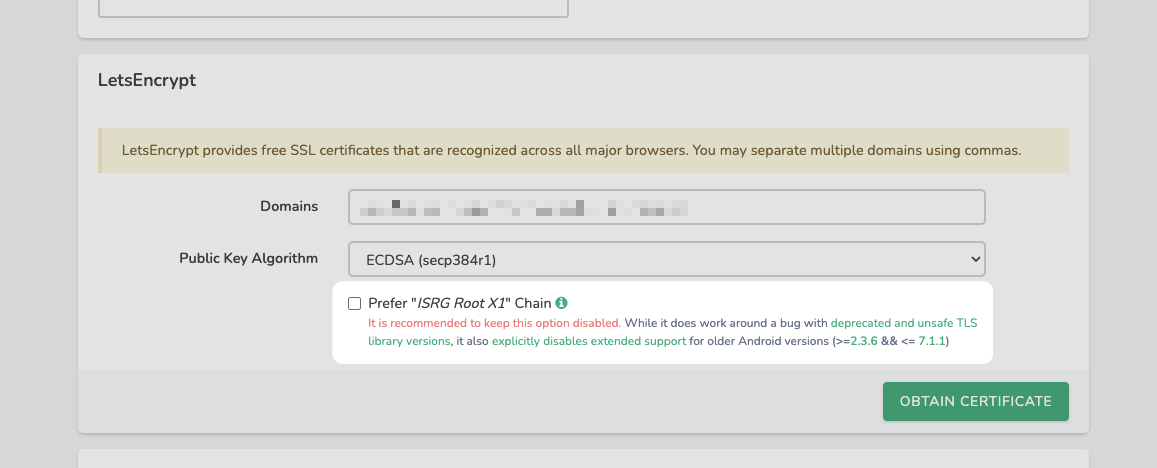 To solve this issue, today's release of Laravel Forge gives you the ability to make a choice, and explicitly allows you to Prefer the "ISRG Root X1 Chain".
To solve this issue, today's release of Laravel Forge gives you the ability to make a choice, and explicitly allows you to Prefer the "ISRG Root X1 Chain".
By selecting this option, Forge will instruct Let's Encrypt to only create a certificate for the ISRG Root X1 certificate, and to not include the DST Root CA X3 certificate. This has a couple of effects:
- The certificate chain is shorter, more efficient, and the SSL handshake is faster.
- Better IoT-device compatibility (the aforementioned OpenSSL bug is avoided)
- Android (>= 2.3.6 && <= 7.1.1) users will not be able to visit your website.
While all of the above might seem like pros rather than cons, do keep in mind that there is still a large volume of Android users (roughly 30%) that are using devices without a way to upgrade to a compatible version. As such, at least for now, both we as well as Let's Encrypt themselves are recommending against using this option for most people.
If you don’t have a Forge account, now is a great time to sign up! Forge allows you to painlessly create and manage PHP servers which include MySQL, Redis, Memcached, database backups, and everything else you need to run robust, modern Laravel applications.